In the first article in this series “The cryptography behind the currency; an introduction.”, we looked at the two core cryptographic primitives which are the basis of Bitcoin: Digital Signatures and Hash Functions. If the Bitcoin network is our finished dish, then our cryptographic primitives are our ‘vegetables’.
In this article we will go into further depth of just how our vegetables have been uniquely implemented into the world’s first successful peer-to-peer digital money scheme (Bitcoin).
Visualising the peer-to-peer network
To explore the technology further we should visualise the Bitcoin network. Unlike a normal client-server (centralised) set-up, all the nodes on the network are connected to their nearest peers who are connected to other peers and so on, giving us a distributed network.
Decentralised vs. Distributed: Bitcoin is said to be decentralised as it does not rely on a single centralised system to function, however the network itself is a distributed network. These terms are usually used interchangeably so it’s useful to know the difference.
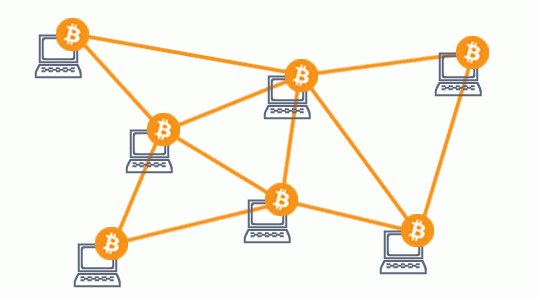
[Figure 1: Diagram of a distributed network]
As you can see, it looks like a web of sorts, where every node holds the same copy of our blockchain ledger and speak to each other to arrive at consensus for every new block.
The bitcoin network itself is peer-to-peer, meaning that every node on the network is equal, it runs over TCP and has a random topology. When joining the network as a node you connect with a ‘seed’ node, and ask it which nodes it has peered with and then go from there.
Transacting on the Bitcoin network
In this section we will go through the mechanics of Bitcoin transactions to show how our Digital Signatures and Hash Functions are being used in practice.
Creating a wallet
We know from Digital Signatures that our friend will be transferring us money to our public key. We must have the ability to create and manage our public and private key in order to redeem our Bitcoin. This is why wallet control and key management is the most important aspect of cryptocurrencies – if somebody knows our private key then they OWN our Bitcoin!
We lose our private key we lose our Bitcoin!
The easiest way of creating a Bitcoin wallet is via a Wallet Software. This software sits on your local computer and manages the details of your keys. First, our wallet software creates a signature/verification key pair in line with the Elliptic Curve Digital Signature Algorithm (ECDSA). Wallet software often gives you the ability to create multiple key pairs so that every transaction is executed with a different key; this can support anonymity.
To create your Bitcoin address the software generates an ECDSA key pair and then hashes it using SHA-265 and RIPEMD160 to achieve a shorter address, this is then Base-58 encoded into letters and numbers so it can be easily read.
Example Bitcoin address generation (under the hood):
256-bit ECDSA signature key (hex): f2f474a0e59f77694086b019431369e2387b719a8a4805ff66015b492f8a2248
512-bit ECDSA verification key (hex): 04f8652b2f48eb362a3d0fc756472ce6ddff004a321a708723fccfde3218034f0a05caae8ef06a15ad3157462405a121acdd58c84ff2bbd87ea76210cbb560b266
Once you have generated your public key this is then hashed with SHA-256 (crypto vegetable!), then hashed again using RIPEMD160.
256-bit Hash SHA-256 EC verification key: fe875970e24999dbb9c35306328d4c5eb09969c5fd47442ccdb12ebc694ef5bf
160-bit Hash RIPEMD160 the result: 4ac38bcdafcb6ab6c91fb987d0e4540aa2875666
When you provide your public key to somebody it’s easier to give it to them in a more readable string or a QR code – so Bitcoin does just this! Base-58 encoding converts from a binary number to a set of 58 characters; uppercase, lowercase letters, and digits.
Base-58 result = BITCOIN ADDRESS: 17pKFygDzGmR8as8pHkikhyAPaSvmRz7aB
Some people even run through a lot of possible signature/verification key pairs so that they end up with a base-58 encoded “vanity” string. Such as…
1MickRulesZm8as8pHkikhyAPaSvmRz7aB
Read the full set of steps in Bitcoin address creations here
Receiving and Spending Bitcoin
There is a key concept which needs to be understood before we can detail how you can spend your BTC; Bitcoin doesn’t keep records of account balances, it keeps only the transactions. Spending Bitcoin works when you can verify a transaction you have been sent by a previous entity, therefore you can spend it.
The Bitcoin ledger on the blockchain is append-only – you can only write data to this ledger and it remains there forever, unchanged and has a complete history of every transaction.
If you have been transferred BTC but you have not spent that BTC then you will have “credit” on your account. In reality it is just transactions in the ledger linking to your Public Key which are marked as ‘unspent’.
Using our previous example of our friend Mick who lives in Australia, he needs these things to spend and receive BTC:
- Bitcoin Address (Mick_BTCaddress) = 1MickRulesZm8as8pHkikhyAPaSvmRz7aB
- Verification (Public) Key (Mick_PubKey) – hashes to the bitcoin address above
- Digital Signature (Mick_Sig) – signing the transaction using Mick’s private key and proving Mick owns the relevant public key.
Simplified, imagine Mick and his friends have gone out for dinner they agreed Mick would pay the entire bill from his Bitcoin account. During the dinner they each transfer Mick their portion of the bill which looks like:
INPUTS:
Abby_Sig transferred 0.1 BTC to Mick_BTCaddress
Bruno_Sig transferred 0.1 BTC to Mick_BTCaddress
Charlie_Sig transferred 0.1 BTC to Mick_BTCaddress
Dylan_Sig transferred 0.1 BTC to Mick_BTCaddress
When these transactions have been confirmed in the blockchain they exist as ‘unspent transactions’. Mick can now transfer the restaurant the total bill.
OUTPUTS:
Mick_Sig transferred 0.4 BTC to PizzaExpress_BTCaddress
Each bitcoin transaction reads like a script which lists a number of inputs and outputs, where Mick_Sig is used to verify the BTC sent to Mick_BTCaddress – essentially the script is saying “these four 0.1 BTC transactions can be redeemed by a public key that hashes to Mick_BTCaddress, along with a signature from the owner of that public key.”
After transferring 0.4 BTC to Pizza Express the original input transactions are marked as ‘spent’.
Mmmhmm Pizza…
Blockchain consensus and the double spending problem
Previous digital money technologies harnessed the use of Digital Signatures, which provides us with that all important non-repudiation when promising a payment to an entity. However, with just Digital Signatures a problem can arise; how does the network know whether I have already spent my money? Can I “double-spend” my money by sending two payments to two different parties?
Recall our bitcoin network of nodes, these are our Bitcoin Miners, they are peered with each other and reach consensus on valid transactions. But how do they all come to consensus? This is where the blockchain comes in…
Bitcoin miners:
- Listen for transactions on the network
- Maintain the blockchain and listen for new blocks
- Assemble a candidate block
- Find a nonce that makes their block valid
- Hope their block is accepted
- Profit
When transactions are made on the network they are first broadcast to all peer nodes and so on. Then it is put into a transaction pool and the Miner takes a group of said transactions and tries to solve a cryptographic puzzle in order to achieve the block reward of 25 BTC.
To achieve the block reward the Miners increment the nonce into a hash which starts with a certain amount of leading zeros. The amount of leading zeros is changed via an algorithm which calculates that it must take 10 minutes to mine a block.
H( Prev. Hash + Nonce + Transactions ) = 00000000xxxxxxxxxxxxxxxxxxxxxxxxx
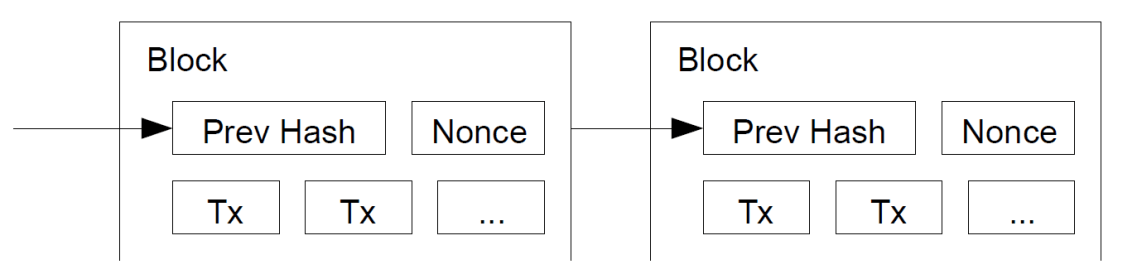
[Figure 2: A Peer-to-Peer Electronic Cash System https://bitcoin.org/bitcoin.pdf]
When they have “solved the cryptographic puzzle” they broadcast their block to their peers and the rest of the network of nodes who judge whether your block is valid. If they deem it valid they will continue to mine the blockchain on top of your block (using your hash within their block). This is network-wide consensus as the majority of the network will be mining on top of the longest chain of blocks, achieving global consensus.
Merkle Trees
Onto our next cryptographic vegetable, well in this instance its more of a puree!
Inside of every block there are several transactions, however it would be very inconvenient to have to hash all the transactions in the block together just to validate one transaction later down the line. This is where Merkle trees become very useful.
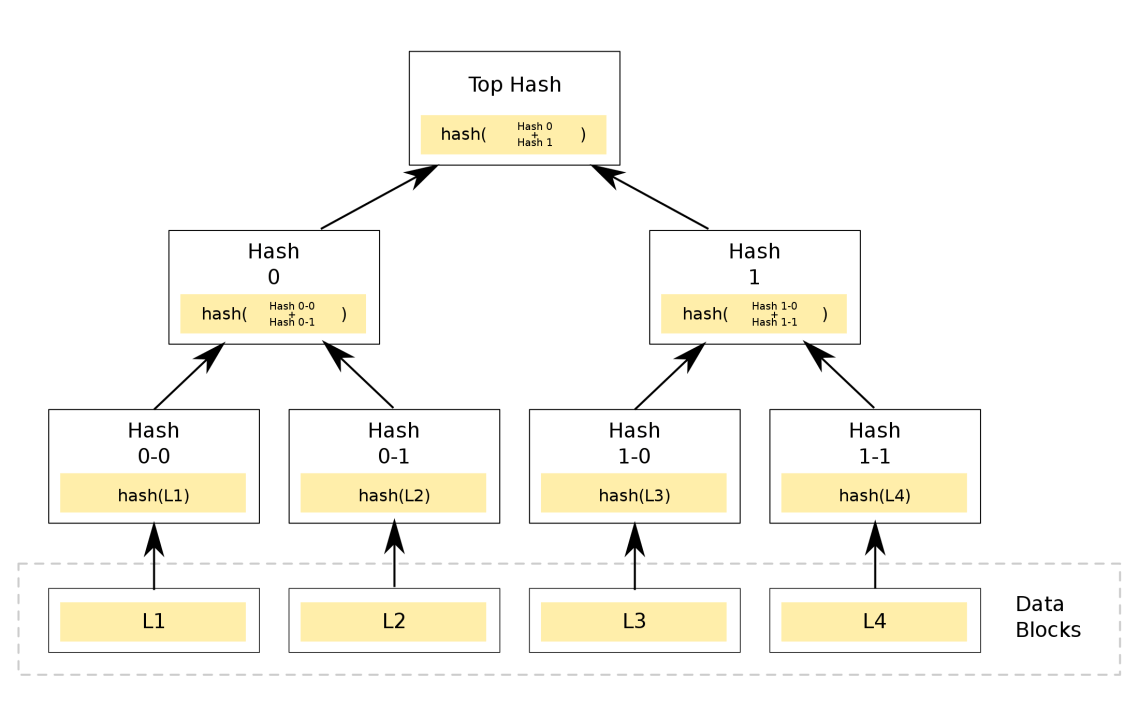 [Figure 2: By Azaghal – Own work, CC0, https://commons.wikimedia.org/w/index.php?curid=18157888]
[Figure 2: By Azaghal – Own work, CC0, https://commons.wikimedia.org/w/index.php?curid=18157888]
All the transactions (L1, L2, L3, L4) are hashed to H(L1), H(L2), H(L3) and H(L4). Then these are hashed together in pairs so H(H(L1)+H(L2)) and H(H(L3)+H(L4)) then these are hashed together to make a root hash. This root hash is then included in the block shown below.
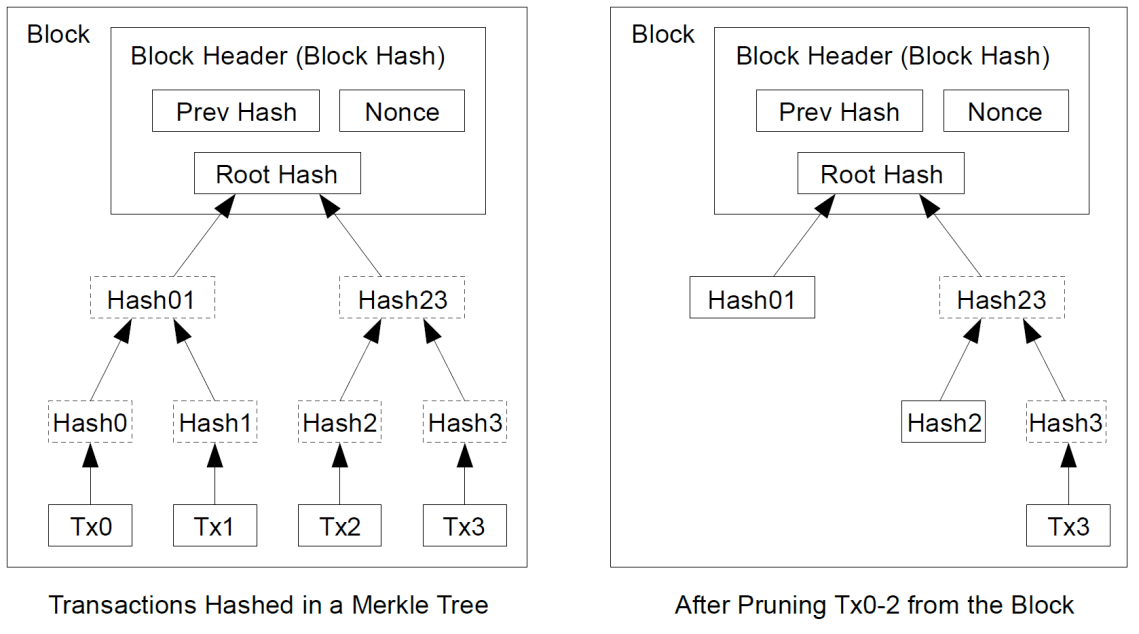
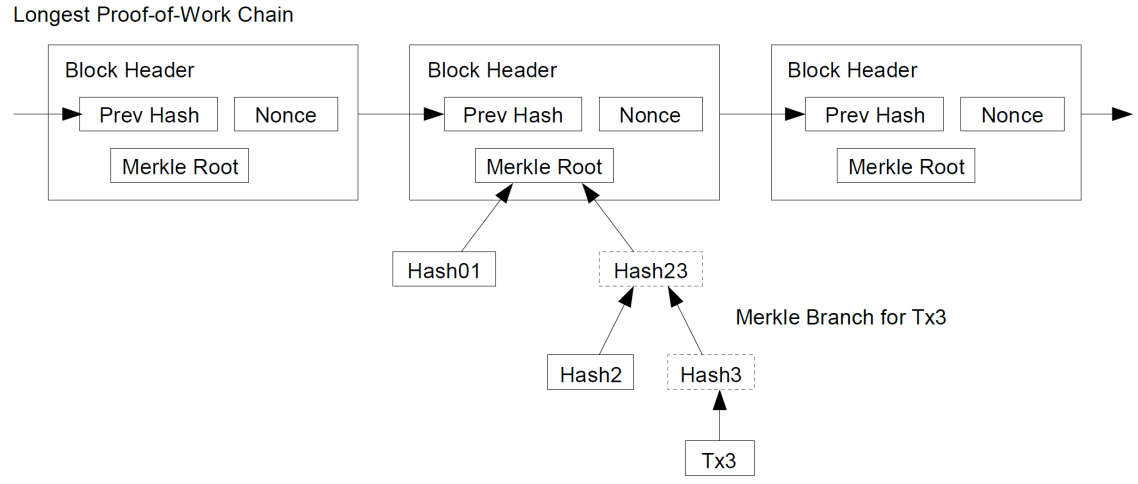
[Figure 4: Bitcoin: A Peer-to-Peer Electronic Cash System https://bitcoin.org/bitcoin.pdf]
Looking at [Figure 4], it’s later down the line and we want to verify a specific transaction (Tx3) in a block. You can see, the only information we need is Tx3, Hash2, Hash01 and Root Hash instead of the whole block of transactions to hash together – this is a fantastic vegetable and used widely in lightweight Bitcoin nodes to verify transactions.
The double spending problem
We can call the longest chain of blocks the “longest consensus chain” – this is where (assuming over half the nodes are honest) it will contain only valid transactions and no double spends.
[Figure 5: Bitcoin: A Peer-to-Peer Electronic Cash System https://bitcoin.org/bitcoin.pdf]
A good example of a double spend attack is imagining Mick back in Pizza Express after just purchasing dinner. Whilst in the restaurant the transaction went into the blockchain and Pizza Express were satisfied the bill was paid. However, immediately after leaving Mick rushes to his computer and starts to mine another block on the blockchain on the block previous to that of his Pizza Express transaction. His new block contains a transaction which sends those bitcoins back to himself instead of Pizza Express.
Now, if Mick can keep his block in the long-term consensus chain then he has successfully achieved a free dinner and made some profit off his mates in the process. At this point it could go either way and the rest of the network of miners could indeed take Mick’s chain as the longest, but it’s not guaranteed.
Let’s say Mick succeeds and Pizza Express are very upset and vow never to take payments via BTC again. But let’s remember, for Mick to mine one block on his own would have been a massive feat, but to mine up to six blocks in a row would be near to impossible as he doesn’t have anywhere near that amount of computing power.
Therefore, really all Pizza Express have to say is “we will take BTC payments, but you must wait an hour to confirm the payment before leaving our establishment”. It’s not perfect but it’s something!
Incentive of miners
Now, what would happen if a malicious actor mined a block? Well, they can’t steal anybody else’s bitcoins that’s for sure – because Digital Signatures 😉 But they can double-spend their own BTC.
If you’re malicious and you’ve got access to enough computing power to mine a block and you achieved said block, you have just earned yourself a block reward of 25 BTC and all the transaction fees. At the moment 25 BTC is around $160,000 :-O
It’s this incentive around our proof-of-work (hashing puzzles) which keeps Bitcoin miners honest as it is more profitable to pay honestly in the game than maliciously.
Conclusion
Phew that was crypto heavy!! I hope you enjoyed getting into some of the nitty gritty.
My final piece of the ‘BANG for your Bitcoin’ series will be titled ‘The blockchain demystified’ where we will cover Etherium’s blockchain with Blockchain 2.0 Smart Contracts and applications of blockchain technology outside of currency.
Sources:
Bitcoin: A Peer-to-Peer Electronic Cash System; Satoshi Nakamoto; https://bitcoin.org/bitcoin.pdf
A lot of material from this article was taken from the book “Bitcoin and Cryptocurrency Technologies, A Comprehensive Introduction” by Narayanan, Bonneau, Felten, Miller and Goldfeder. Here is a link to buy it on Amazon https://www.amazon.co.uk/Bitcoin-Cryptocurrency-Technologies-Comprehensive-Introduction/dp/0691171696 – I would HIGHLY recommend it.
